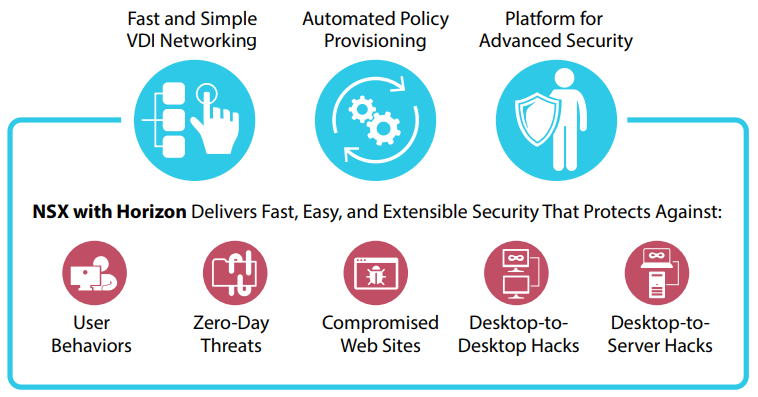
Everyone talks about NSX features for Data center only, what about Desktop Infrastructure?. NSX with Horizon going to be a perfect combination for the customers who are looking for Nex-Gen Desktop experience as it overcome physical network challenges. NSX offers an extensible platform that can be integrated with best-in-class capabilities from an established ecosystem of security partners. By dynamically adding services, virtual desktop security can be easily extended take advantage of malware protection, anti-virus production and advanced threat detection. VMware NSX for Horizon brings speed and simplicity to virtual desktop infrastructure (VDI) networking, with policies that dynamically follow virtual desktops.
Many organizations implement desktop and application virtualization to improve client computing security and deliver greater enterprise mobility. Centralizing desktops and applications protects data at rest, prevents unauthorized application access, and provides a more efficient way to patch, maintain and upgrade images.
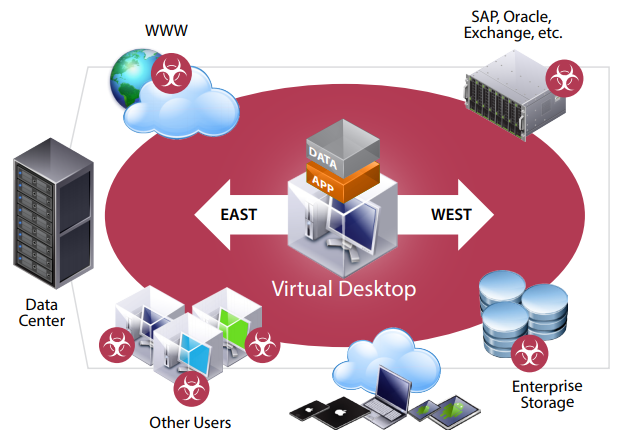
East-West Security Concerns Within the Data Center
However, with desktop and application virtualization, new security concerns can arise behind the data center firewall—where hundreds or even thousands of desktops reside. These desktops sit in close proximity to other users and mission-critical workloads, making them much more susceptible to malware and other attacks. These attacks can move from desktop to server, exposing a large attack surface within the data center.This “east-west” threat scenario is a common one affecting many customers today, particularly those with stringent security and compliance mandates. Organizations seeking to administer networking and security policy that persistently follows users and workloads have also traditionally incurred a significant investment in a hardware-centric architecture that is CapEx-intensive, complex to operate, and slow to adapt to the typical dynamic business environment. VMware NSX for Horizon effectively secures east-west traffic within the data center, while ensuring that IT can quickly and easily administer networking and security policy that dynamically follows end users’ virtual desktops and apps across infrastructure, devices, and locations.
VMware NSX for Horizon improves desktop virtualization security and helps address east-west threats by enabling administrators to define policy centrally. That policy is then distributed to the hypervisor layer within every vSphere host, and automatically attached to each virtual desktop as soon as the desktop is created. To secure virtual desktops and adjacent workloads within the data center, VMware NSX implements “microsegmentation,” giving each desktop it’s own perimeter defense. This “shrink-wrapped security” uses VMware NSX distributed virtual firewalling capability to police traffic to and from each VM, eliminating unauthorized access between desktops and adjacent workloads. If the virtual desktop moves from one host to the next, or across the data center, policy will automatically follow it. In this video we take a look at some typical desktop configurations, their possible vulnerabilities and where we can reduce the chance of attack by employing some simple changes without impacting desktop performance with NSX.
“Be social and share it with social media, if you feel worth sharing it”